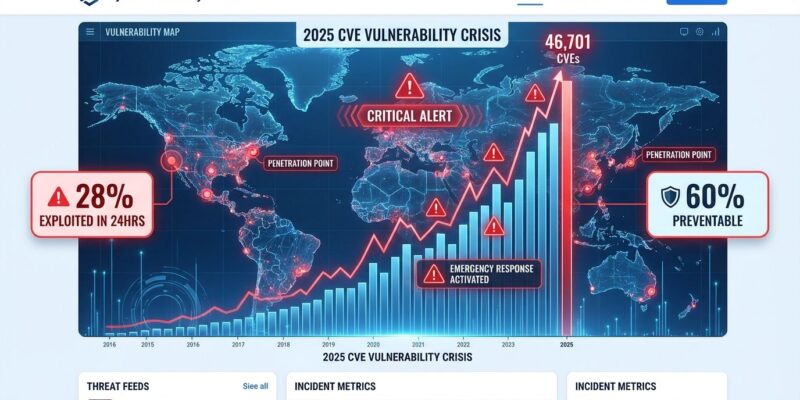
The software security industry published 46,701 CVEs in 2025 through December 24—an 18% year-over-year increase that brings the daily average to 130 new vulnerabilities. However, volume isn’t the real crisis. The problem is speed: 28% of these vulnerabilities get exploited within 24 hours of disclosure, while enterprise patch cycles run 30 to 60 days. The most damning statistic exposes the system’s failure: 60% of breached organizations had patches available for the exploited vulnerabilities but never applied them.
This isn’t a security problem. It’s a broken incentive structure masked as one.
Attackers Move at Machine Speed, Defenders at Human Speed
When a CVE drops, the race starts immediately. Research from VulnCheck and Recorded Future shows 28.3% of vulnerabilities exploited within the first 24 hours, with 50-61% seeing weaponized exploit code within 48 hours. In the first half of 2025 alone, 161 distinct vulnerabilities saw active exploitation—151 for malware deployment, 73 for ransomware. Moreover, state-sponsored actors accounted for over half of this activity.
The attack profile favors speed: 69% of exploited vulnerabilities required no authentication, and 30% enabled remote code execution. These aren’t sophisticated attacks requiring deep research. They’re opportunistic strikes against known weaknesses, executed at machine speed.
Meanwhile, organizations remediate just 16% of vulnerabilities monthly on average. Typical enterprise patch cycles take 30-60 days for standard vulnerabilities, with a target of 15 days for critical ones. Consequently, even if security teams hit that 15-day target for every critical CVE—an impossible standard—attackers still have a two-week head start. It’s not a fair fight. It’s a fundamental mismatch between the speed at which threats materialize and the pace at which organizations can respond.
The Patching Paradox: Patches Exist But Go Unapplied
The Ponemon Institute found that 60% of organizations experiencing a breach in 2024 admitted the root cause was an unpatched vulnerability with a known fix. Furthermore, the Verizon DBIR echoed this: more than half of breaches traced back to vulnerabilities that had patches available for months or even years. This isn’t a technical failure—the patches exist. It’s an organizational failure to deploy them.
Why? Start with alert fatigue. Security teams face 46,701 CVEs in 2025, with 38% rated High or Critical severity. That’s roughly 8,300 “urgent” vulnerabilities demanding immediate attention. NinjaOne’s survey found 71% of IT and security professionals find patching overly complex and time-consuming. Add IT staff shortages, hybrid workforces scattering endpoints across home networks, compatibility testing overhead, and the constant tension between security teams demanding patches and IT teams defending uptime—and you get a system that collapses under its own weight.
The National Vulnerability Database (NVD) hasn’t helped. It stumbled in 2024 and still hasn’t analyzed roughly half of that year’s vulnerabilities, creating intelligence gaps for organizations that rely on NVD’s CVSS scoring. Consequently, when the infrastructure meant to help prioritize vulnerabilities can’t keep pace with disclosure volume, the entire system shows its age.
If Everything Is Critical, Nothing Is
January 2025 set a record with 4,278 CVEs in a single month. The year maintained a pace of 130+ vulnerabilities disclosed daily. Of the 46,701 total CVEs, 1,773 carried Critical severity ratings (CVSS 9-10), and 6,521 scored High (CVSS 7.0-8.9). Thus, security teams theoretically need to analyze 8,300+ urgent vulnerabilities this year alone—on top of existing backlogs, ongoing operations, and new projects.
The signal-to-noise ratio has become untenable. SecurityInfoWatch’s 2025 analysis noted that “CVE overload is unmanageable, with tens of thousands disclosed annually and no way for teams to patch everything.” Security teams end up firefighting across massive vulnerability backlogs, trying to satisfy boards, auditors, and insurers that they’re secure—while critical issues get lost in the noise and remediation gets delayed where it matters most.
More CVE disclosures should theoretically improve security. Instead, they’re creating alert fatigue that obscures actual threats. The CVE system was designed for an era of manageable disclosure volumes. It can’t scale to 50,000 vulnerabilities annually.
Decades-Old Bugs Still Dominate Exploitation
MITRE’s 2025 CWE Top 25 list, based on 39,080 CVE records from June 2024 to June 2025, reveals an uncomfortable truth: Cross-Site Scripting (XSS) holds the #1 spot for the second consecutive year with a score of 60.38—more than double the next entry. Similarly, SQL Injection climbed to #2 with a score of 28.72. Cross-Site Request Forgery (CSRF) took #3.
XSS has been on the OWASP Top 10 since 2003—22 years. SQL injection prevention has been well-documented since 1998. These aren’t obscure edge cases or novel attack vectors. They’re fundamental security flaws that every developer should know to avoid, supported by decades of tooling, training, static analysis, and code review processes. Yet they remain the most exploited weaknesses in 2025.
This exposes a systemic failure that goes deeper than patch management. The industry isn’t learning from past mistakes. Security education, automated scanning tools, and security-conscious frameworks all exist—yet basic vulnerabilities persist. The problem is structural, not technical.
What Actually Works: Risk-Based Prioritization
The current approach—attempt to patch all CVEs—is obsolete. Organizations need fundamental rethinking. Two approaches show promise:
CISA’s Known Exploited Vulnerabilities (KEV) catalog focuses exclusively on vulnerabilities with confirmed active exploitation. The federal Binding Operational Directive (BOD) 22-01 requires all federal civilian agencies to remediate KEV vulnerabilities within prescribed timeframes. CISA strongly recommends all organizations—not just federal agencies—use the KEV catalog for prioritization. It cuts through the noise by focusing on threats actively used in the wild, not theoretical severity scores.
Exposure validation tests which vulnerabilities are actually exploitable in your specific environment. Instead of relying on generic CVSS scores, organizations run tests against production-like environments to identify viable attack paths. Additionally, this evidence-based approach separates real threats from noise, letting teams focus resources on reducing actual risk rather than checking boxes.
Automation becomes mandatory, not optional. Attackers exploit at machine speed—defenders need to respond at machine speed. Automated patch management, AI-driven vulnerability prioritization, and automated testing reduce the time between disclosure and remediation. Organizations that continue relying on manual processes and human-speed patch cycles will keep appearing in breach statistics.
The Bottom Line
The 60% statistic—breaches from unpatched vulnerabilities with available fixes—reveals the real crisis. This isn’t a shortage of patches or a lack of security awareness. It’s a system generating so much noise that critical signals get buried. When everything is urgent, nothing gets fixed.
The tools exist. The patches exist. What’s missing is effective prioritization and deployment. Organizations can’t patch 46,701 vulnerabilities. Therefore, they need to ruthlessly prioritize the ones that actually matter—the ones actively exploited or exploitable in their specific environment—and automate response wherever possible.
More CVEs won’t save us. Smarter prioritization might.