X11’s security flaw isn’t a bug you can patch—it’s architectural design from 40 years ago. Right now, any application on your Linux desktop can spy on any other: reading password manager keystrokes, capturing banking screenshots, recording everything you type. No exploits needed, just normal X11 API calls. Moreover, Xorg’s million-line C codebase can’t fix this. The X.org Foundation is still patching CVEs for vulnerabilities introduced before X11R6.1 was released in 1996. Phoenix, a modern X server written from scratch in Zig and trending on Hacker News today with 234 points, takes a different approach: ground-up rewrite with application isolation by default, memory safety without garbage collection overhead, and hardware-accelerated rendering already working.
X11’s Architectural Security Problem
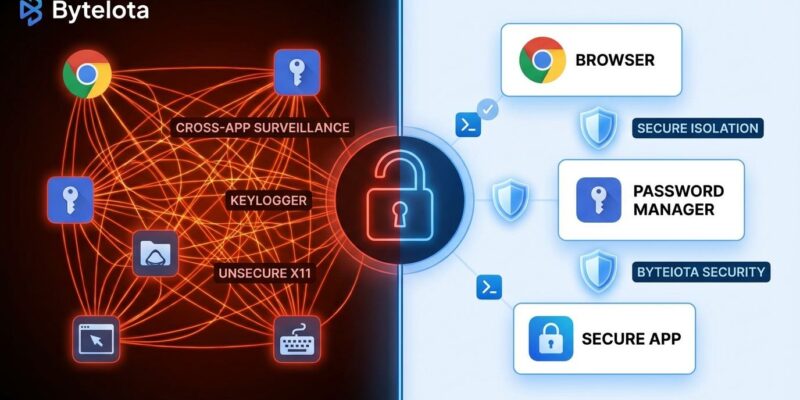
Under X11, everything shared one input space. Any client that registers for raw keyboard events can see keystrokes across your whole session, not just its own window. The input stream is mirrored to every client listening—no isolation whatsoever. Malicious browser extensions can read your password manager. Random applications can screenshot your banking session. Supply-chain compromised dependencies can keylog your SSH credentials.
Furthermore, the X11 SECURITY extension tried to fix this in the 1990s with a binary classification: trusted versus untrusted clients. It broke too much legitimate functionality to be practical. When you run multiple sandboxed programs, they can still spy on each other. The extension shipped disabled by default and stayed that way.
The problem runs deeper than code quality. X11’s trust model assumes all applications are friendly—a design that predates malicious browser extensions, supply-chain attacks, or zero-trust security. After four decades of accumulated technical debt, the Xorg codebase security is “worse than it looks,” according to security researchers. CVEs keep surfacing for buffer overflows and integer overflows dating back to before 1996. You can’t patch your way out of architectural problems.
Phoenix’s Security-First Redesign
Phoenix reimplements the X11 protocol with one core principle: applications are isolated from each other by default. They can only interact through explicit user-approved GUI prompts. Screen recorders work, but only after you approve which specific windows they can record. Password managers remain isolated. Cross-app keylogging becomes impossible.
The clever part: when applications request cross-app access they shouldn’t have, Phoenix returns dummy data instead of errors. This maintains backward compatibility with X11 clients while enforcing security boundaries. Applications don’t crash—they just can’t spy anymore. It’s the security model X11 should have had from the start, applied without breaking the protocol.
Additionally, Phoenix ditches X11’s historical baggage. UTF-8 strings replace ISO Latin-1 encoding. GrabServer—a notorious security risk—has no effect. Network transparency features from the 1980s are gone. Mandatory X11 protocol features like legacy font operations aren’t implemented. The result: a leaner, more secure display server that still runs X11 applications.
Current status: Phoenix can render simple applications using GLX, EGL, or Vulkan graphics with full hardware acceleration. It’s not production-ready—this is early-stage development by a solo developer. However, the fact that hardware-accelerated rendering already works proves the concept is technically viable.
Why Zig for Display Servers
Display servers sit between your applications and GPU drivers, handling 60 frames per second of graphics rendering, low-latency input events, and efficient memory allocation. They’re foundational infrastructure that runs for months without restart. Two requirements dominate: memory safety to prevent vulnerabilities, and zero overhead to maintain performance. Garbage collection pauses are unacceptable at 60fps.
Zig provides memory safety without runtime overhead. The compiler catches array out-of-bounds access and null pointer dereferences at compile-time. The debug allocator automatically detects use-after-free and double-free bugs, printing stack traces for memory leaks. Unlike Rust’s strict borrow checker, Zig trusts developers more while still providing meaningful safety guarantees.
The critical advantage: C interoperability. Zig has a built-in C compiler and can directly import .h header files and call C functions without any binding code or FFI complexity. This matters enormously for display servers, which must interface with GPU drivers, X11 protocol libraries, and hardware abstraction layers—all written in C. Rust can do this, but it’s significantly more complex.
Zig’s comptime system moves type checking and validation to compile-time, catching bugs before the program runs while generating zero-overhead code. It replaces the complexity of C++ templates and Rust macros with a single, unified feature: arbitrary Zig code execution at compile-time. For display server performance, this distinction changes everything. Every microsecond counts at 60fps.
The Memory-Safe Systems Programming Wave
Phoenix isn’t an isolated experiment. Specifically, the same memory safety crisis that pushed the Linux kernel to adopt Rust permanently in 2025 and Microsoft to rewrite Windows with 180,000 lines of Rust drives Phoenix’s existence. Consequently, seventy percent of Microsoft’s security vulnerabilities trace back to C/C++ memory issues. Ninety percent of Android CVEs correlate to memory safety problems.
The Linux kernel officially adopted Rust as a permanent core language at the 2025 Kernel Maintainers Summit, ending years of experimental status. Fedora and Ubuntu are already enabling Rust in their default kernels. Meanwhile, Microsoft went further: Galen Hunt’s December 24, 2025 LinkedIn post outlined the goal to “eliminate every line of C and C++ from Microsoft by 2030.” The first Rust code shipped in Windows 11 back in May 2023. Amazon, Facebook, Google, and Mozilla have all adopted Rust for systems programming.
Zig offers a different answer than Rust—simpler, more C-compatible, but still memory-safe. Phoenix proves it works for OS-level infrastructure. The industry isn’t standardizing on one memory-safe language; instead, it’s validating multiple approaches to the same fundamental problem: C/C++ is too dangerous for critical systems.
Why Not Just Use Wayland?
Wayland already solved X11’s security problems with a ground-up redesign. Input isolation stops background keylogging. Screen capture requires user approval. Each client runs in its own sandbox. Major distributions ship it by default: Debian 10+, Fedora 34+, Ubuntu 18.04+. KDE and GNOME have mature Wayland support.
So why Phoenix? Because according to Wayland’s own documentation, “the majority of X11 applications haven’t been modified and ported to Wayland, and the uptake and migration is expected to be long and slow.” XWayland provides compatibility, but with limitations. Utilities like xrandr and xdotool don’t have direct Wayland equivalents. Edge-case workflows still require X11.
Phoenix addresses a different use case: users who need X11 application compatibility but refuse to accept 1980s security architecture. It’s not competing with Wayland—it’s proving that X11 and security aren’t mutually exclusive.
Key Takeaways
- Phoenix demonstrates that secure X11 is technically feasible through application isolation by default and GUI permission prompts for cross-app interactions
- Zig proves viable for OS-level infrastructure with its balance of memory safety, C interoperability, and zero-cost abstractions through comptime
- The memory-safe systems programming trend spans the Linux kernel (Rust permanent adoption in 2025), Microsoft Windows (180K lines of Rust by 2030), and now Phoenix
- Solo developer sustainability remains a question—display servers require decades of maintenance that enterprises like X.org Foundation provide
- Phoenix validates multiple approaches to memory safety beyond Rust, showing that simpler languages with better C interop can work for foundational infrastructure
Read more about Microsoft’s Rust adoption for systems programming and explore the Zig comptime system for compile-time code execution.