The “Shift Left” Era Is Over
DevSecOps is ditching “shift left,” the security mantra that’s dominated developer thinking for a decade. In 2025, the industry is embracing “shift everywhere”—a more mature approach that distributes security across the entire development lifecycle instead of cramming it all into early stages. The shift left promise was simple: catch vulnerabilities early, ship secure code. But it created as many problems as it solved, burning out developers with security noise and missing critical runtime threats.
What “Shift Everywhere” Actually Means
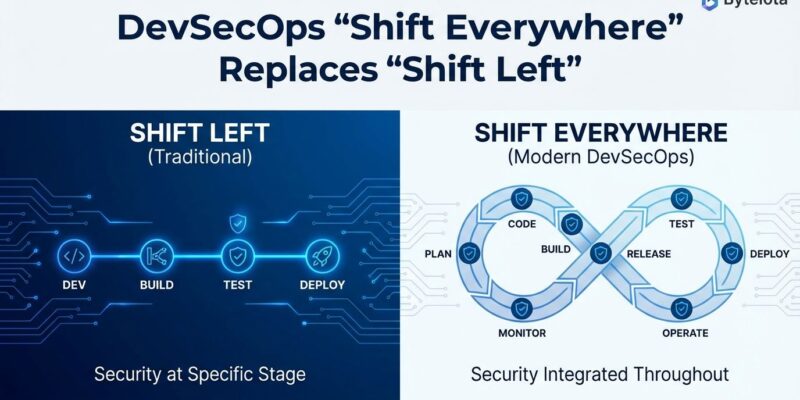
“Shift everywhere” integrates security at every development stage—not just early. According to industry predictions for 2025, DevSecOps is evolving beyond the shift-left paradigm to embrace applying the right security tools at the right stages of the development cycle.
Security happens in the IDE (lightweight scans), pull requests (automated checks), CI/CD pipelines (comprehensive gates), and runtime production (active monitoring). Each stage gets the right level of security analysis, not all security dumped upfront.
In your IDE, lightweight SAST catches obvious flaws without blocking flow. Pull requests trigger automated SCA and SAST checks before merge. CI/CD runs comprehensive DAST, compliance scans, and deployment gates. In production, RASP (Runtime Application Self-Protection) monitors execution and blocks threats in real-time. Production threat intelligence feeds back to development, updating scanning rules automatically. Security learns and improves continuously.
Why Shift Left Failed
Shift left’s fatal flaw: it tried to make developers security experts. They never asked for that job. Developers got stuck with early-stage security testing, vulnerability remediation, policy compliance, AND their actual work—writing code. That’s not reducing toil, that’s multiplying it.
Worse, shift left generated noise instead of intelligence. Vulnerability scanners flag libraries with CVEs but don’t know if that code is reachable in production, behind a feature flag, or even executed. As DevOps.com notes on shift left’s limitations, developers spent hours chasing theoretical risks while missing critical ones. Tools generated alerts, not actionable intelligence.
Shift left focused solely on pre-deployment security. It missed runtime vulnerabilities, supply chain attacks after deployment, infrastructure misconfigurations, and production anomalies. You can’t shift ALL security left because some threats only exist at runtime. Static analysis can’t predict every attack vector that emerges in live traffic.
Perhaps most damning: shift left had no feedback loop. Security should learn from production incidents. But shift left was one-directional—scan code early, deploy, done. No mechanism to feed runtime intelligence back to development pipelines. Security never got smarter.
How to Implement Shift Everywhere
Start with multi-stage security pipelines. In your IDE, install security plugins (SonarLint, Snyk IDE extensions) that highlight critical issues like SQL injection patterns or hardcoded secrets without blocking your workflow. Think spell-check for security, not a full audit.
For pull requests, use pre-push hooks to run local SAST and SCA before commits hit your repo. GitHub Actions or GitLab CI can automatically scan PRs with inline fix suggestions right in the diff. This is where automated CI/CD security integration catches issues before merge.
In CI/CD, run the full security suite as deployment gates: SAST for code analysis, SCA for dependency scanning, DAST for runtime testing, secrets detection, container scanning, compliance checks. This is where thorough analysis belongs—not in your IDE slowing you down.
For production, deploy RASP tools that embed sensors in your application. They monitor execution in real-time, detecting and blocking SQL injections, API abuse, and command injections as they happen. Runtime Application Self-Protection (RASP) acts like an internal security net catching what perimeter defenses miss. The RASP market is growing 28.82% annually, reaching $2.02 billion in 2025—because the industry finally admits shift left failed at runtime security.
What Developers Actually Get
Less noise, more signal. AI-powered tools like Jit and Snyk now prioritize vulnerabilities by actual risk—is the code reachable? Is data sensitive?—instead of just severity scores. Fewer false positives, more actionable alerts.
You’re not becoming a security expert. You’re getting smart automation at every stage. Lightweight scans in your IDE won’t block flow. Heavy analysis runs in CI/CD where it belongs. Security isn’t all on your shoulders upfront anymore. The IDE catches obvious mistakes, PR automation handles dependency checks, pipeline gates enforce policies, runtime monitors production.
Modern tools suggest fixes inline. Not just “vulnerability detected”—here’s the patch to apply. GitHub Copilot Security, Snyk auto-fix, and similar tools cut remediation time from hours to minutes.
This Isn’t a Trend—It’s Table Stakes
Major vendors are making moves. Fortinet acquired Lacework for cloud-native app protection. Contrast Security launched Application Vulnerability Monitoring, correlating static analysis with runtime exploits. GitHub and GitLab are integrating native security across their entire platforms.
Generative AI is the catalyst enabling shift everywhere at scale. AI agents automate security checks, prioritize by real risk, suggest remediation, and orchestrate workflows across every development stage. Within two years, security will be mostly automated across the entire lifecycle.
If you’re still doing shift-left-only security in 2025, you’re shipping vulnerabilities to production. The industry took a decade-long detour with shift left. We’re finally back on track.


